Authentication
PolicyServer Management UI is a secure application and requires user authentication to administer policies. There are two ways to authenticate to the PolicyServer UI:
Login as a root administrator
Login with Single Sign-On (SSO)
Root Administrators
Root administrators are configured in application settings in the host section:
"PolicyServer": {
"host": {
"identity": {
"admins": [
{
"username": "<username>",
"password": "<encoded password>",
"displayName": "<display name for root admin>"
}
],
}
}
}
The first root administrator is created when you set up your PolicyServer host configuration using the wizard. You’ll use this username and password to login at the root login page:
Root administrators have access to all features of the PolicyServer included in the license and enabled in the configuration, including the ability to add Policy administrators using the Admin features.
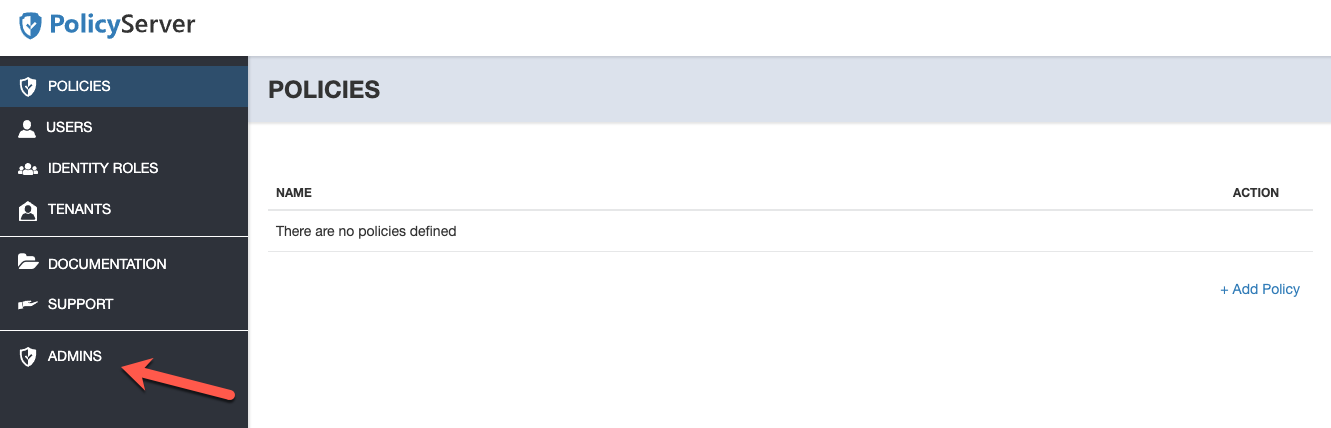
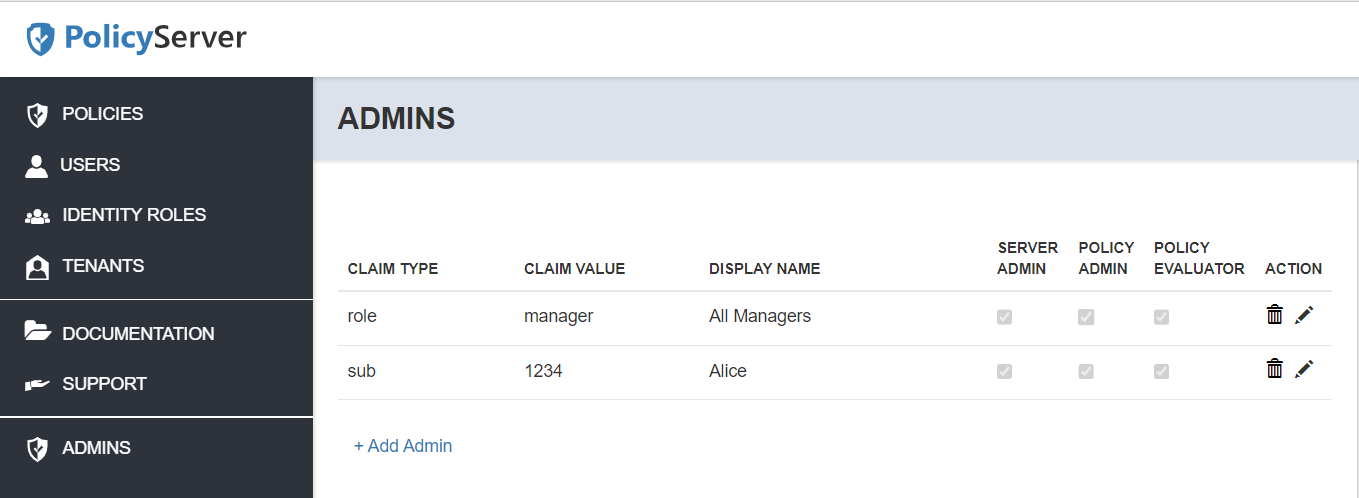
PolicyServer Administrators
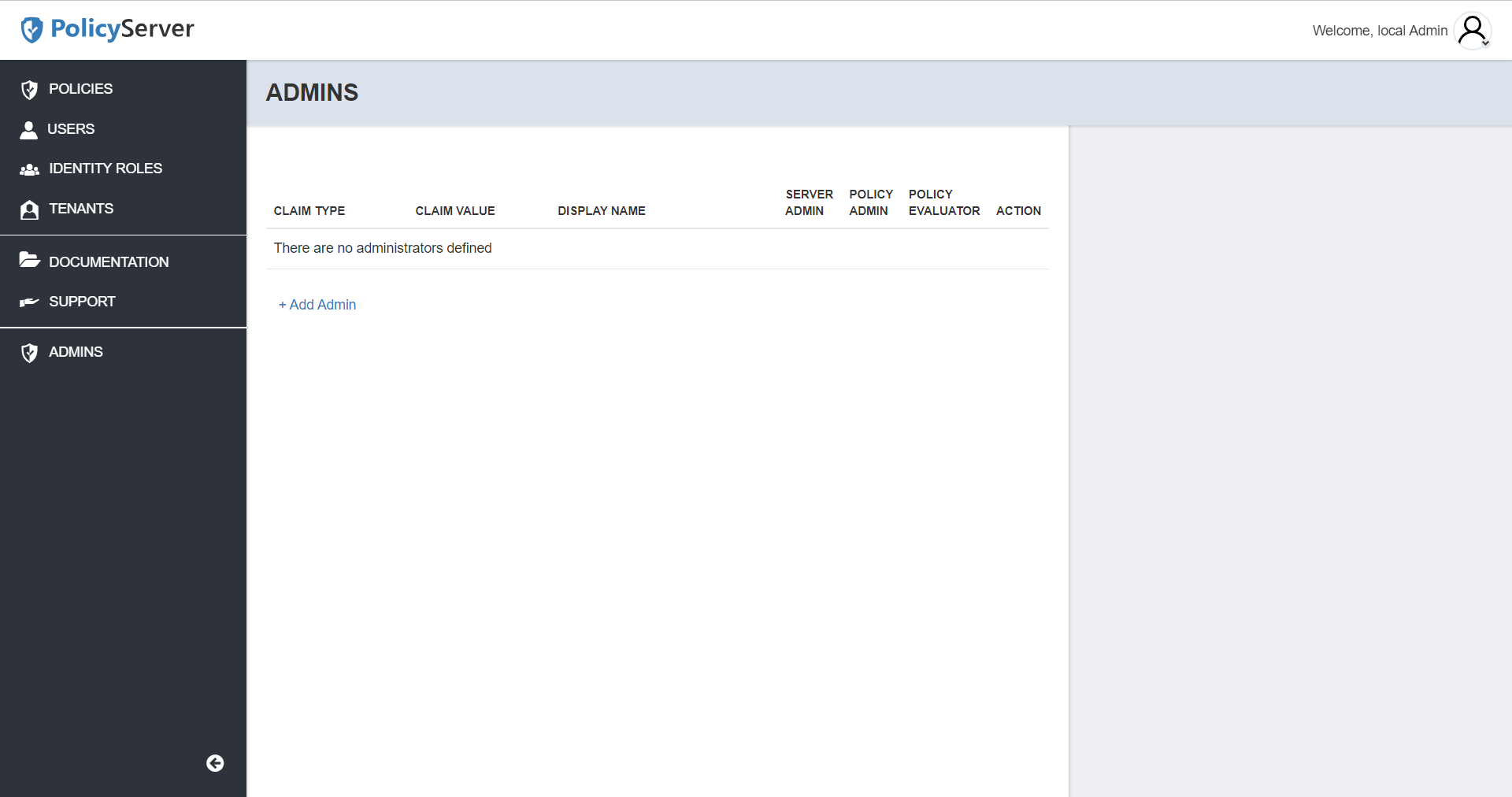
PolicyServer administrators can be added through the Admins area of the PolicyServer UI. Currently, only root administrators have access to this feature.
Warning
You can configure PolicyServer administrators in advance of enabling Single Sign-On to PolicyServer, however, those identified users will not be able to login until Single Sign-On is enabled so that they can login at the configured identity provider.
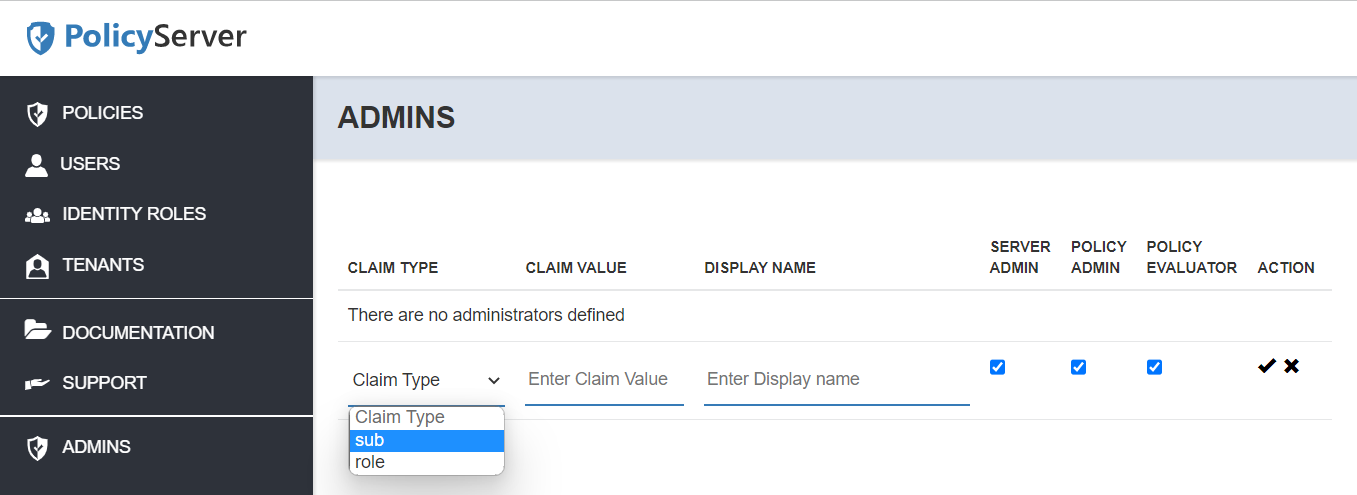
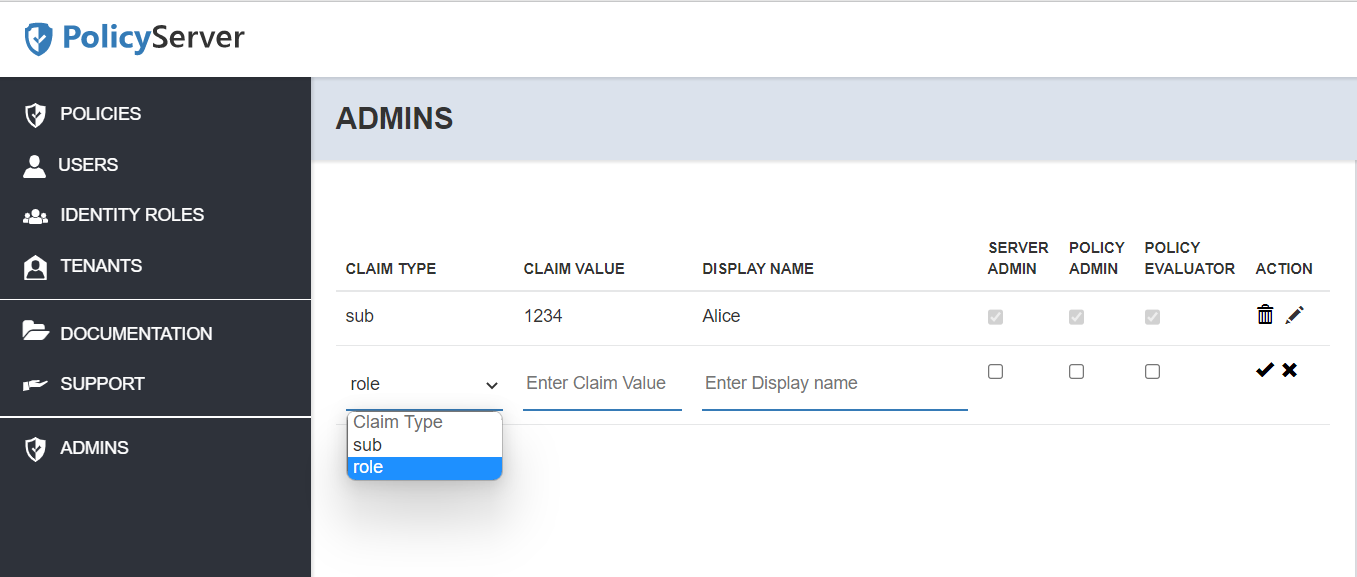
Adding a PolicyServer administrator by their user id
To add a PolicyServer administrator by their user id, indicate the sub or user id value you are expecting for that user in the Claim Value. You can also add a display name.
Adding a PolicyServer administrator by mapping a role
To add one or more Policy administrators by mapping an identity role, indicate the role name or value you are expecting for PolicyServer administrators in the Claim Value. You can also add a display name for this permission assignment.
Removing a PolicyServer administrator
To remove a PolicyServer administrator, click the delete icon or trashcan for that row.
Configure PolicyServer administrator permissions
Each administrator can have one or more of the below permissions
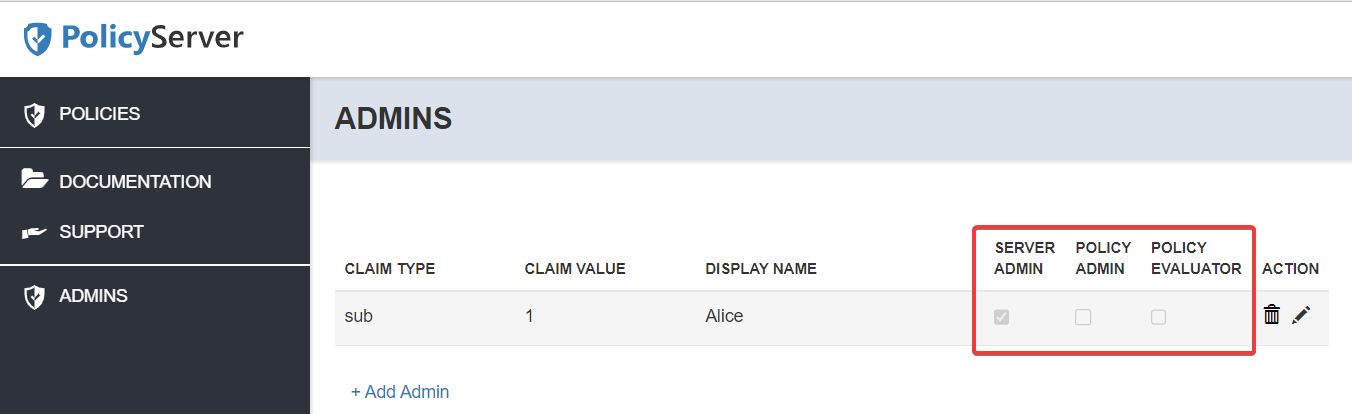
Server Admin
The server admin can only take action in the Admin tab and manage the other administrators but he cannot manage policies
Policy Admin
The policy admin can only take actions on the policies sections and its child sections, but will not see the Admin menu Item
Policy Evaluator
The policy evalutor can only use the runtime api and will not be able to take any actions on the management UI and will not see the admin menu item
Setting up Single Sign-On
You can enable Single Sign-On so that PolicyServer authenticates approved user from your identity provider of choice. Any compliant OpenID Connect identity provider can be configured as the identity provider for the PolicyServer UI.
You establish trust with your identity provider by setting the base-address in the sso configuration section, e.g. in JSON:
"PolicyServer": {
"host": {
"identity": {
"sso": {
"openidconnect": {
"authority": "https://duendesoftware-ps-test.azurewebsites.net",
"clientid": "login"
}
},
}
}
}
Warning
This will change the configuration of PolicyServer so that now, unauthenticated users will be redirected to the identity provider. To reach the root administrator login page you can navigate to /root at your PolicyServer UI. From there you will continue to be able to login as a root administrator if there are any valid administrators in the configuration.
Configuration settings
The configuration section for sso has the following settings:
"sso": {
"openIdConnect": {
"authority": "https://duendesoftware-ps-test.azurewebsites.net",
"clientId": "",
"clientSecret": "",
"responseType": "id_token|code",
"scope": "openid profile",
"nameClaimType": "name",
"subClaimType": "sub",
"roleClaimType": "role"
},
"federatedLogoutPrompt":true
},
Setting |
Description |
|---|---|
|
Indicates the base address of the identity provider. |
|
Indicates the client id of PolicyServer UI at the identity provider. |
|
Indicates the secret of the identity provider if this is needed for the protocol flow (e.g. code flow). |
|
Indicates the expected response type. Use id_token for implicit flow, code for code flow (with or without PKCE). |
|
Indicates the scopes to provide to the identity provider as part of the OpenID Connect authorization request. |
|
Indicates the claim type that should be used for the display name of the user, if the claim type name is not used. |
|
Indicates the claim type that should be used for any user id mappings, if the claim type sub is not used. |
|
Indicates the claim type that should be used for any role mappings, if the claim type role is not used. |
|
Instruct the UI to show confirmation prompt before the logout action giving the user the option to cancel or proceed. |
Setting up external issuer
Setting up an external issuer will allow you to delegate the token issuance for the clients and the users to an external issuer. The configuiration for the external issuer is as follows::
"PolicyServer": {
"host": {
"identity": {
"externalTokenIssuer": {
"authority": "<issuer authority>",
"runtimeApiScope": "<policyserver.runtime>",
"managementApiScope": "<policyserver.management>",
"RemoveSubjectIdForMachineClients": [true|false],
"claimMappings": {
"ClientIdClaimTypes": [ "azp" ],
"SubClaimTypes": [ "azp" ],
"ScopeClaimTypes": [ "roles" ]
}
},
"sso": {
"federatedLogoutPrompt": true,
"openidconnect": {
"authority": "<issuer authority>",
"clientid": "<client id>",
"clientSecret": "<secret>",
"responseType": "code",
"responseMode": "query",
"scope": "openid profile roles"
}
},
}
}
}
Configuration settings
Setting |
Description |
|---|---|
|
Indicates the base address of the external token issuer. |
|
The defined runtime client scope in the external issuer. |
|
The defined management client scope in the external issuer. |
|
Flag to either include the subject claim value in the claim principal or remove it in case the client is a machine client. |
|
The claim mapping object is where you can define the the claim types for clients, subject, and scope. |
|
Indicates the claim type that should be used for the get the client_id, if claim_id is not used. |
|
Indicates the claim type that should be used for any user id mappings, if the claim type sub is not used. |
|
Indicates the claim type that should be used for any scope mappings. |
|
SSO object is same as described in the previous section. |